
Case Report of Email Spying
*Corresponding Author(s):
Ruiz RCTI Renato Archer, Campinas, Department Of Crime, Research Instuite In Campinas, Brazil
Tel:+55 19 3746-6000,
Email:rodrigosruiz@outlook.com
Abstract
This case report is about Brazilian researchers that did have their e-mail invaded by Uk Ministry of Defence with cooperation from Microsoft Corp. The work show details of the invasion and steps that permitted this discovery.
Keywords
Cold War; Data Leakage; Email; MoD UK; Outlook; Privacy; Spy; Terrorism
INTRODUCTION
In times where the opponent was a state, as, during the Second World War, all efforts were made to ensure secure communication. During the war itself, the Allies deciphered the German encryption machine, beginning a real obsession with how to decode cyphers of the opponents and, at the same time, create powerful cyphers for their own use. The pigeons have been replaced by emails. Today, instant messages are the most common form of communication between companies, individuals and governments. In that fraction of a second between sending and receiving messages via email, who else will have access to them? In response, service operators include guarantees within their contracts about user privacy, along with the use of SSL [1] to protect communications.
James Bond 007, is also associated with real-life versions of the National Security Agency (NSA) of United States of America [2], the CIA [3] and the extinct KGB (FSB) [4]. Meanwhile, the Edward Snowden case [5] has resulted in geopolitical consequences for, as well as caused discomfort and financial damages among, former allies as evidence of espionage on a large scale are no longer limited to the declared enemy. After 9/11, the game of espionage changed again. Fear changed the way of life around the world. Privacy and confidentiality are characteristics, which, when lost, result in financial losses and demand a considerable effort to regain them, although recovery is virtually impossible. This issue is well characterized by Scheneier [6]. Society has opened up its privacy in exchange for the promise of more security. Who decides which particular individual should be the focus of monitoring focus, and in what form? In January 2015, the magazine Science published a special issue titled “The End of Privacy” [7]. Large companies are often blamed for providing data on people and institutions indiscriminately to governments without appropriate legal actions. As there are no effective means of control, businesses and individuals essentially depend on the trust that people have in these large companies that hold records on us. On 11th July 2013, the British newspaper The Guardian [8] published the contents of top-secret documents, showing that Microsoft works in conjunction with the NSA and the FBI, helping these agencies to circumvent new encryption procedures in its products, including Outlook. Microsoft was given the right to reply by the newspaper: “We have clear principles which guide the response across our entire company to government demands for customer information for both law enforcement and national security issues. First, we take our commitments to our customers and to compliance with applicable law very seriously, so we provide customer data only in response to legal processes.”
THE GAME’S AFOOT
Despite our indignation towards this breach in our email security, rather than scare the hacker, we decided to exploit the situation and expand our knowledge of email privacy. During the first months of 2015, email communications were made using controlled messages in order to protect the integrity of our research, while our curiosity about the hacker continued to increase. By monitoring the situation, we obtained Outlook access reports (see Figure 1). As can be seen in Table 1, IP address properties were established through consultations with ARIN [9] and RIPE.net Figure 1 [10].
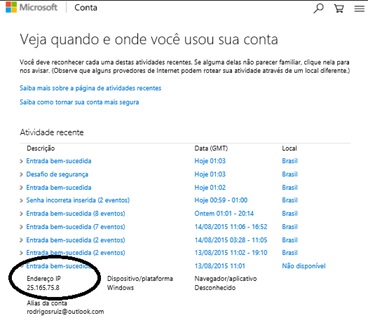
Figure 1: Microsoft Outlook® access report and IP 25.165.75.8, which is the property of the UK’s Ministry of Defence.
The password used to protect the account assigned at the time of the incidents was regarded as “strong,” that is, it contained a great number of numbers, upper and lower case letters, and special characters, which is a format typically used in IT (e.g., “f5Gr$ekslanhjo”). It would be unthinkable that a corporation, which is one of the symbols of America, would be institutionally involved with an unfriendly foreign government. During recent years, the entire world’s media has regularly referred to the NSA in the context of any espionage action, control and invasion of privacy against people, businesses and governments around the world.
These reports have also shown that there is at least another player in the game, the UK, as seen in Figures 2 and 3, Table 1. The evidence, which is indisputable, point to actions of the UK in the USA, specifically in Microsoft. In the search for an answer, we contacted the UK’s Ministry of Defence [11], who was evasive in response, as can be seen in Figure 3. When the UK Government answers by saying, “We do not confirm and we do not deny,” it alerts everyone to the privacy and security of the UK’s business, industrial and scientific secrets.
|
Date/time |
IP |
Owner |
Local |
|
15-01-2015 13:22 |
157.56.238.188 |
Microsoft Corporation |
Redmond |
|
29-01-2015 14:39 |
132.245.80.92 |
Microsoft Corporation |
Redmond |
|
02-02-2015 04:10 |
132.245.32.12 |
Microsoft Corporation |
Redmond |
|
02-02-2015 04:10 |
132.245.32.11 |
Microsoft Corporation |
Redmond |
|
03-02-2015 04:49 |
132.245.11.4 |
Microsoft Corporation |
Redmond |
|
03-02-2015 14:15 |
132.245.32.4 |
Microsoft Corporation |
Redmond |
|
09-02-2015 12:15 |
198.11.246.181 |
Softlayer/F-Secure |
Chantilly/ Washington |
|
20-03-2015 10:41 |
25.163.90.11 |
Ministry of Defence, UK |
London |
|
20-03-2015 16:46 |
25.160.164.153 |
Ministry of Defence, UK |
London |
|
31-07-2015 20:04 |
25.165.74.23 |
Ministry of Defence, UK |
London |
|
13-08-2015 11:01 |
25.165.75.8 |
Ministry of Defence, UK |
London |
|
30-10-2015 09:24 |
25.165.118.133 |
Ministry of Defence, UK |
London |
|
27-11-2015 11:28 |
25.165.74.25 |
Ministry of Defence, UK |
London |
Table 1: List of IP addresses through which the email account was accessed improperly accessed.
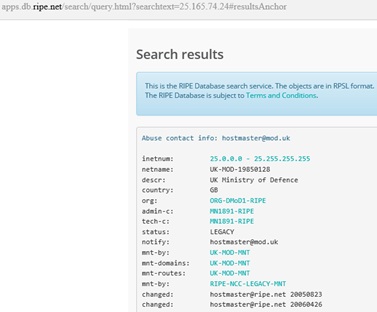 Figure 2: The RIPE Network Coordination Centre, the organization responsible for coordinating IP registries in Europe, assigns the range 25.0.0.0 to 25,255,255,255 to the UK’s Ministry of Defence.
Figure 2: The RIPE Network Coordination Centre, the organization responsible for coordinating IP registries in Europe, assigns the range 25.0.0.0 to 25,255,255,255 to the UK’s Ministry of Defence.
 Figure 3: Response from the UK’s Ministry of Defence when asked if it authorized the intrusion into the researcher’s email account or whether its own computers had been hacked by third parties, thereby allowing access.
Figure 3: Response from the UK’s Ministry of Defence when asked if it authorized the intrusion into the researcher’s email account or whether its own computers had been hacked by third parties, thereby allowing access.
When questioned about these incidents, Microsoft [12] provided the following protocols: 1076B89D; 9023A4AE; 4FB0DD02; B860A2E9; 102FD43B. On 18 December 2015, Microsoft Computer Emergency Response provided the response as shown in Figure 4. When Microsoft declared that the access simply involves a Microsoft server-to-server call, we might ask the following:
- Are Microsoft Outlook servers embedded in the UK’s Ministry of Defence infrastructure? If so, why?
- In Figure 6, we present an example of human interaction in Washington DC in which a user typed in a wrong password a few days before London received access to the email account. Why would Microsoft imagine that an automated server system would type in wrong passwords?
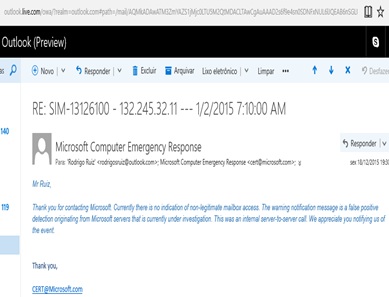 Figure 4: Microsoft’s response that the incident in question is just a false positive with regard to its own server-to-server communications: “Thank you for contacting Microsoft. Currently, there is no indication of non-legitimate mailbox access. The warning notification message is a false positive detection originating from Microsoft servers that are currently under investigation. This was an internal server-to-server call. We appreciate you notifying us of the event.”
Figure 4: Microsoft’s response that the incident in question is just a false positive with regard to its own server-to-server communications: “Thank you for contacting Microsoft. Currently, there is no indication of non-legitimate mailbox access. The warning notification message is a false positive detection originating from Microsoft servers that are currently under investigation. This was an internal server-to-server call. We appreciate you notifying us of the event.”
This answer does not correspond to the information that Microsoft published on its site [12] about the security and privacy of Outlook Figures 5,6 and 7. On the same page Microsoft, says:
“When you tell us that you don’t recognize an activity, it’s possible that a hacker or a malicious user has gotten access to your account. To help protect your account, we’ll walk you through several steps, including changing your password and reviewing and updating your security info.”
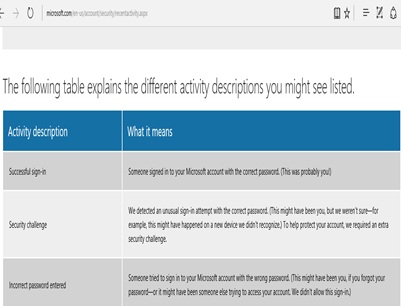 Figure 5: Microsoft describes on the user’s page [12] the different activities relating to an Outlook access report.
Figure 5: Microsoft describes on the user’s page [12] the different activities relating to an Outlook access report.
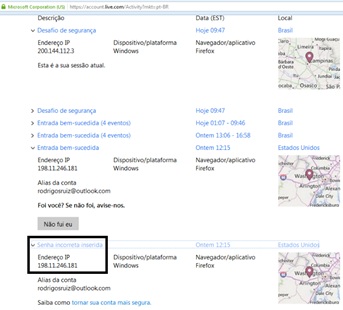 Figure 6: A wrong password was typed in by a human in Washington DC a few days before London got access to the email account. “Senha incorreta inserida” is Portuguese for “Wrong password typed”.
Figure 6: A wrong password was typed in by a human in Washington DC a few days before London got access to the email account. “Senha incorreta inserida” is Portuguese for “Wrong password typed”.
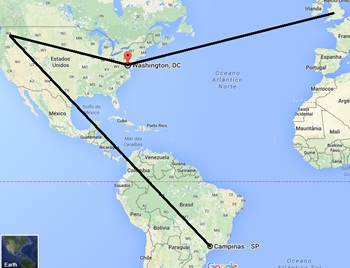 Figure 7: The way of shame, starting in Brazil, where the real user accessed their webmail and where the hacking took place in Microsoft, connecting in Washington DC and finally arriving in London. Im-age from Google Maps.
Figure 7: The way of shame, starting in Brazil, where the real user accessed their webmail and where the hacking took place in Microsoft, connecting in Washington DC and finally arriving in London. Im-age from Google Maps.
MORE QUESTIONS THAN ANSWERS
What are the conditions that might have led to the UK becoming involved in this incident? Or was the UK Government also a victim, ashamed to admit that it had been hacked? And did Microsoft fall prey to one of its employees? What is the impact of this type of espionage in the world on researchers and the general public? Are thousands of researchers vulnerable to the shady methods and almost unlimited resources of organized hackers? How many patents are at risk? Is the crime no longer about stealing, but simply getting caught? The Los Angeles Times reported in 2001 that the relationship between scientific research and intelligence agencies did not cool off after the Cold War as previously thought. But, while these researchers continue to fully cooperate with their intelligence masters [13], they should not forget that the same person who pays the wages of these scientists may also be reading their emails on a daily basis.
REFERENCES
- What is SSL? (2019) SSL and Digital certificates, SSL/TLS.
- National Security Agency central security service, USA.
- Central Intelligence Agency, Washington, D.C, USA.
- The russian governoment, Federal Security Service, Russia.
- NSA FILES: DECODED, What the revelations means for you.
- Schneier B (2012) Securing Medical Research: A Cybersecurity Point of View. Science 336: 1527-1529.
- The end of privacy (2015). Science AAAS.
- Microsoft handled the NSA access to encrypted messages.
- American registery for internet numbers.
- Ripe Network Co-Ordination Center.
- Ministry of Defence UK.
- What is the recent activity page? Microsoft (2015).
- Academics and Spies: The Silence that roars, USA.
Citation: Ruiz R, Winter R (2020) Case Report of Email Spying. Forensic Leg Investig Sci 6: 046.
Copyright: © 2020 Ruiz R, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.

