
The Feasibility of Creating a Universal Digital Forensics Framework
*Corresponding Author(s):
Gareth DaviesDepartment Of Engineering And Science, Faculty Of Computer, University Of South Wales, United Kingdom
Email:gareth.davies@southwales.ac.uk
Abstract
Keywords
Digital evidence; Digital forensics; Methodologies; Standardization; Universal Framework
INTRODUCTION
- To identify the justifications for a standard in the subject area of digital forensics
- To identify the barriers to a global standard
- To be able to make recommendations on how to create a single global digital forensics standard
Added to the complexity of digital forensics is the impact of remote and distributed systems as well as the developing technology of artificial intelligence (AI). The challenge is to present evidence with a reliable method; with such a variety of methods a key area for development is the standardization to meet all current and future requirements. This research will concentrate on the current models utilized by investigators and will investigate the analysis already performed to standardize the methods. The sources for this information will be specialist journals such as International Journal of Digital Evidence and articles found on forensic websites, as well as academic books on the subject.
In his book ‘Digital Forensics Threats cape and Best Practices’ John Sammons [2] put together several expert authors to write about specific areas. Mark Pollitt was one of the contributors and he introduced the simplest digital forensics model, the 4-stage model (Figure 1) developed in 2006 by the National Institute of Standards and Technology (NIST).
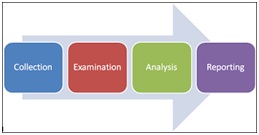
As well as providing an outline of a model he also clearly defines the goals of digital forensic investigation. This is a good start point for any future standard, in understanding the foundation of the role and building from that.
His two goals were:
- To preserve the integrity of the evidence
- To find and make available information of value to the submitter of the evidence.
RESEARCH METHODS
It is hoped that the output of this research will be an understanding and a consensus that a standardized model is required and initiating collaboration between nations across the world to achieve this common goal.
Previous studies of digital forensic methodologies have concentrated on a comparison of what exists and how to improve what exists to make the process more reliable, and thus generate a new methodology. In this project, the aim was different; the intention was to review the comparison literature that exists on digital forensics and develop an understanding of what is the purpose of the investigation methodology. Simultaneously, a review of current trends in Information Technology and the future possible infrastructure changes that may cause barriers for evidence gathering was performed.
STANDARDS
A standard is a structured set of rules, guidelines or characteristics that are a measure of the quality and provide an assurance of the fitness for purpose of an output from a human endeavor. This set of rules, guidelines and characteristics will have been generated from a consensus of experts in the subject field.
Considering the development cycle of the field of digital forensics and the stage that it has currently reached it can be implied that the next stage will be to support the development of automatic processes which would allow for the larger volumes of evidence that are retrieved to be processed more effectively and efficiently. The digital forensic industry is ready for this next stage of evolution.
There are both advantages and disadvantages to the implementation of standards within the industry. The following are some common advantages to standardization:
- Provide a definition of common technological terms
- Allows for individuals to train to the same level of knowledge and expertise
- Ensures that the industry has integrity
- Give confidence to the consumer
- Updated regularly to keep pace with technology
- Ensure that evidence is not mishandled
Standards linked to Digital Forensics
ISO17025 – General Requirements for the Competence of Testing and Calibration Laboratories
ISO27035 – Information Security Incident Management
ISO27037 – Identification, Collection, Acquisition and Preservation of Digital Evidence
ISO9001 – Quality Management Systems
ISO 17025
DISCUSSION
The authors discuss the reasons why no standard had been developed realizing that current models were based on the technology available and were very ad-hoc. These developments have been inspired by the emergence of new technology and the need to be able to analyse data, not from the scientific community, and therefore they are not considered to be reliable and are untrusted in a court of law.
The four models that were discussed were:
- Farmer and Venema [5] 5 steps to dealing with a situation
- K Mandia and C Prosise Incident response methodology
- Department of Justice model
- DFRWS model
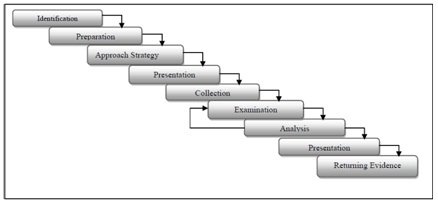
The method is adaptable in its design to permit additional sub-procedures which would support the different classes of digital technology under this model. This would mean that only new sub-procedure Would need to be developed for a new technology, rather than writing a completely new method as is the current trend.
Taxonomy of Computer forensics methodologies and procedures for digital evidence seizure
- Acquire evidence without altering or damaging it
- To authenticate that the copy is the same as the evidence seized
- Analyse the data without altering it.

The article compares three different methodologies, the Basic Forensics Model, the Cyber Tools On-line Search for Evidence (CTOSE) and Data Recovery UK (DRUK). The comparison is provided in the form of tables for the Identification, Acquisition, Analysis and Reporting phases. The tasks are based upon the author’s opinion of what needs to be performed and the article being written in 2006 makes no reference to technology and thus has an advantage that it is generic. It is recognized by the authors that there is a wide diversity of methodologies utilized in digital forensics, but all commonly attempt to provide the same integrity of data. It continues emphasizing that work is needed to provide a standard method for all, that is should be mandatory and a legal requirement which would provide the integrity and reliability that is necessary.
Common phases of computer forensics investigation models
This research was searching to identify the common phases that went across the majority of models; the authors had to make assumptions about similar phraseology linking similar steps. This needs detailed knowledge of all the methodologies to ensure that a phase is not misinterpreted. The authors were able to generically group activities together and came up with a 5-stage model, the result being the Generic Computer Forensics Investigation Model (Figure 4).
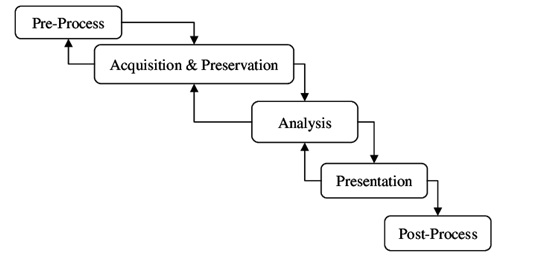
This model was generated from sound scientific analysis, but the analysis lacks consideration of models generated for other digital devices such as mobile phones. This raises the question of whether this model would be generic enough to consider all digital devices. The authors recognized that the process of digital investigation is not a linear one, which allows for investigators uncovering new leads as they analyse evidence and returning to the data gathering stage.
Analyses of the state-of-the-art digital forensic investigation process models
|
|
Reference phases |
DFWRS [4] |
Reith et al. [10] |
DOJ [11] |
Carrier at al.[12] |
Mandia et al. [14] |
Beebe et al. [15] |
Cuardhuain [16] |
Cohen [17] |
Casey & Rose [18] |
ACPO[6] |
|
Phases |
|||||||||||
|
1 |
1.Incident Detection |
1.Identification |
1.Identification |
|
2. Detection and Notification |
2.Detection of the incident |
2.Incident response |
1. Awareness |
|
|
|
|
2 |
First Response |
|
|
|
|
3.Initial response |
2. Incident response |
|
|
|
2.1 Secure and control the crime scene |
|
3 |
Planning |
|
3. Approach strategy |
|
3. Readiness group of phases |
4. Response strategy formulation |
1. Preparation |
|
|
|
1.Preparations for investigations |
|
4 |
Preparation |
|
2.Preparation |
1.Preparation |
3. Readiness group of phases |
1.pre incident preparation |
|
3.Planning |
|
|
1.Preparations for investigations |
|
5 |
Incident scene documentation |
|
|
3.documentaiton of the crime scene |
4.3 document evidence and scene |
|
|
|
|
|
2.1 photograph and document the scene |
|
6 |
Evidence identification |
|
6.examination |
2.recognition and identification |
4.2 survey for digital evidence |
|
|
5. search for and identify evidence |
1. identification |
1. Gather information and make observations |
5.1 The collection phase |
|
7 |
Evidence collection |
2. preservation |
4. preservation |
4. collection and preservation |
4.1 preservation of digital crime scene |
5.duplication |
3. Data collection |
6. collection of evidence |
2. collection |
1. Gather information and make observations |
2.3 Initial collection of volatile data |
|
8 |
Evidence transportation |
|
|
5.packaging and transportation |
|
|
|
7.transport of evidence |
4.transportation |
|
3. Transport |
|
9 |
Evidence storage |
|
|
|
|
|
|
8.storage of evidence |
5.storage |
|
4. Storage |
|
10 |
Evidence analysis |
4.examination |
7.analysis |
6.examination |
4.4 search for digital evidence |
6. investigation |
4. Data analysis |
9. examination of evidence |
6. Analysis |
2. Form a hypothesis to explain observations |
5.2 The analyses |
|
11 |
Presentation |
6.presentation |
8.presentation |
8.report |
4.6 presentation of digital science theory |
10.Reporting |
5. Findings presentation |
11. Presentation of hypothesis |
10. Presentation |
4. Draw conclusions and communicate findings |
|
|
12 |
Conclusions |
7. decisions |
9.Returning evidence |
|
|
9. recovery |
6. Closure |
13. Dissemination of information |
11. Destruction |
|
6.Disclosure |
|
Actionable Principles |
|||||||||||
|
1 |
Interaction with physical investigation |
|
|
3. physical crime scene investigation group of phases |
|
|
|
|
|
|
As principle and set of actions |
|
2 |
Preserving chain of evidence |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
|
3 |
Preserving evidence |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
|
4 |
Information Flow |
|
|
|
|
|
|
Present |
|
|
Present |
|
5 |
Documentation |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
Present |
|
6 |
Obtaining Authorisation |
|
|
2. Confirmation and authorisation |
|
|
|
Present |
|
|
Present |
This analysis shows a scientific methodology has been applied to determining the common phases of models. However, the limitation is that this does not consider models for all types of digital devices e.g. Smart phones. In the current Information Technology environment this is a very important element of any discussion on methodologies for digital forensic investigations. The comparison in providing the actionable principles is an important piece of work, it reflects directly the admissibility of evidence and the actions that must be taken by investigators to ensure evidence is admissible [10].
Comparative Analysis of digital forensic models
|
Steps |
NIJ |
DOJ |
DRFWS |
Abstract |
IDIP |
EIDIP |
SRDFIM |
|
|
|
|
|
|
|
|
|
|
Collection |
X |
X |
X |
X |
X |
X |
X |
|
Examination |
X |
X |
X |
X |
|
|
X |
|
Analysis |
X |
X |
X |
X |
|
|
X |
|
Reporting |
X |
X |
|
|
|
|
X |
|
Preparation |
|
X |
|
X |
|
|
X |
|
Approach Strategy |
|
|
|
X |
|
|
|
|
Preservation |
|
|
X |
X |
X |
X |
X |
|
Presentation |
|
|
X |
X |
X |
X |
X |
|
Identification |
|
|
X |
X |
|
|
X |
|
Return Evidence |
|
|
|
X |
|
|
|
|
Decision |
|
|
X |
|
|
|
|
|
Review |
|
|
|
|
X |
X |
X |
|
Reconstruction |
|
|
|
|
X |
X |
|
|
Documentation |
|
|
|
|
X |
X |
X |
|
Authorisation |
|
|
|
|
X |
X |
X |
|
Survey |
|
|
|
|
X |
X |
|
|
Traceback |
|
|
|
|
|
X |
|
|
Dynamite |
|
|
|
|
|
X |
|
|
Communication |
|
|
|
|
|
|
X |
|
Exploratory Testing |
|
|
|
|
|
|
X |
However, the aim of a standard methodology is to consider all phases of an investigation not just the phase of extraction and analysis which is missing from this analysis.
A new digital investigation framework comparison method
|
Criteria |
Gaining Time |
Reusability |
Evidence Reliability and Consistency |
Evidence Transparence and privacy |
|||||||||
|
Common |
Preparation |
Attribution |
Identification |
Rapport |
Collection |
Presentation |
Examination |
Analysis |
Preservation |
Owner Property |
|||
|
1984 |
|
|
Identification |
|
Acquisition |
Admission |
Evaluation |
|
|
||||
|
2001 |
|
|
Identification |
|
Collection |
Presentation |
Examination |
Analysis |
Preservation |
|
|||
|
2002 |
Preparation |
|
Approach |
Identification |
|
Collection |
Presentation |
Examination |
Analysis |
Preservation |
Returning Evidence |
||
|
2003 |
Readiness |
Deployment |
|
|
Digital crime scene investigation |
||||||||
|
Physical crime scene investigation |
|||||||||||||
|
2004 |
Readiness |
|
Deployment |
Review |
Trace Back |
Dynamite |
|
|
|
||||
|
2006 |
Planning |
Chronology Time |
Triage |
|
User profile |
|
Internet |
Case specific |
|
|
|||
|
2009 |
Planning |
|
Identification |
|
Reconnaisance |
Transport |
Analysis |
Proof |
|
|
|||
|
2010 |
Preparation & Reporting |
Attribution |
Detection of Evidence |
|
Collection |
Preservation |
Examination |
Analysis |
Presentation |
|
|
||
These four key criteria can be seen to reflect part of the APCO [13] principles. This analysis is different because it is focused on tasks that should happen for evidence to be admissible in court. The article proposes a new model which does offer an iterative approach which is essential in digital forensic investigations. The model is designed with two outputs:
- The preservation of the evidence - this is essential in a court of law
- The expert witness statements
Commonality of conclusions
Barriers
- Relevance
- Authenticity
- Not hearsay or admissible hearsay
- Best evidence
- Not unduly prejudicial
- Can be costly for all organisations to attain a standard and its relevant certification
- If a standard is voluntary it does not have to be followed and the industry remains in a flux position.
- Standards can be slow to evolve
- Standards can conflict globally
- Put restrictions on the innovative industries
- Can still be misinterpreted
- Can be cumbersome and increase time spent on a task
- Not enough support to implement them
- Difficult to understand, may be written in technical language
- Cannot confirm an expert’s competence
FEASIBILITY
- Typical legal requirements
- Legal Authorisation
- Digital Evidence Relevance
- Digital Evidence Authenticity
- Digital Evidence Integrity
- Digital Evidence Reliability
CONCLUSION
There is one common outcome from all these comparisons, which is that it is essential to have a global standard method to allow digital evidence investigations to be considered scientifically sound. Although it is agreed that this is important and that there is a consensus on the need of a standard as well as the basic function of the standard, there is no focus from any formal group to expend the time to develop a standard.
RECOMMENDATIONS FOR FUTURE RESEARCH
REFERENCES
- Altoe R (2016) Digital Forensics in an eDiscovery World. Science Direct 6: 85-98.
- Sammons J (2016) Digital Forensics Threatscape and Best Practices.
- Crime Scene Forensics LLC. (2018) History of Finerprints.
- Reith M, Carr C, Gunsch G (2002) An examination of Digital Forensic Models. International Journal of Digital Evidence 3: 1-12.
- Venema D (1999) Computer Forensics Analysis Class Handouts.
- Prosise C, Mandia K (2001) Incident Response Investigating Computer Crime.
- Sansurooa K (2006) Taxonomy of computer forensics methodologies and procedures for digital evidence seizure. Australian Digital Forensics Conference.
- Yusoff Y, Ismail R, Hassan Z (2011) Common phases of computer forensics investigation models. International Journal of Computer Science and Information Technology 3: 17-31.
- Valjarevic A, venter H (2012) Analyses of the state of the art digital forensic investigation process models. Institute of Electrical and Electronics Engineers. 74-83.
- Casey E (2011) Digital evidence and computer crime forensic science, computers and the internet.
- Jafari F, Shafique Satti R (2015) Comparitive Analysis of digital forensic models. Journal of Advances in Computer Networks 3: 82-86.
- Takwa O, Belgacem C, Adel D (2016) A new digital investigation framework comparison method. International Journal of Computer Techniques. 3: 6-10.
- Officers (2012) ACPO Good Practice Guide for Digital Evidence. London: ACPO.
- Antwi Boasiako A, venter H (2017) A model for Digital Evidence Admissability assessment. Advances in Digital Foresics. 23-38.
Citation: Davies G, Smith K (2019) The Feasibility of Creating a Universal Digital Forensics Framework. Forensic Leg Investig Sci 5 : 027.
Copyright: © 2019 Gareth Davies, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.

